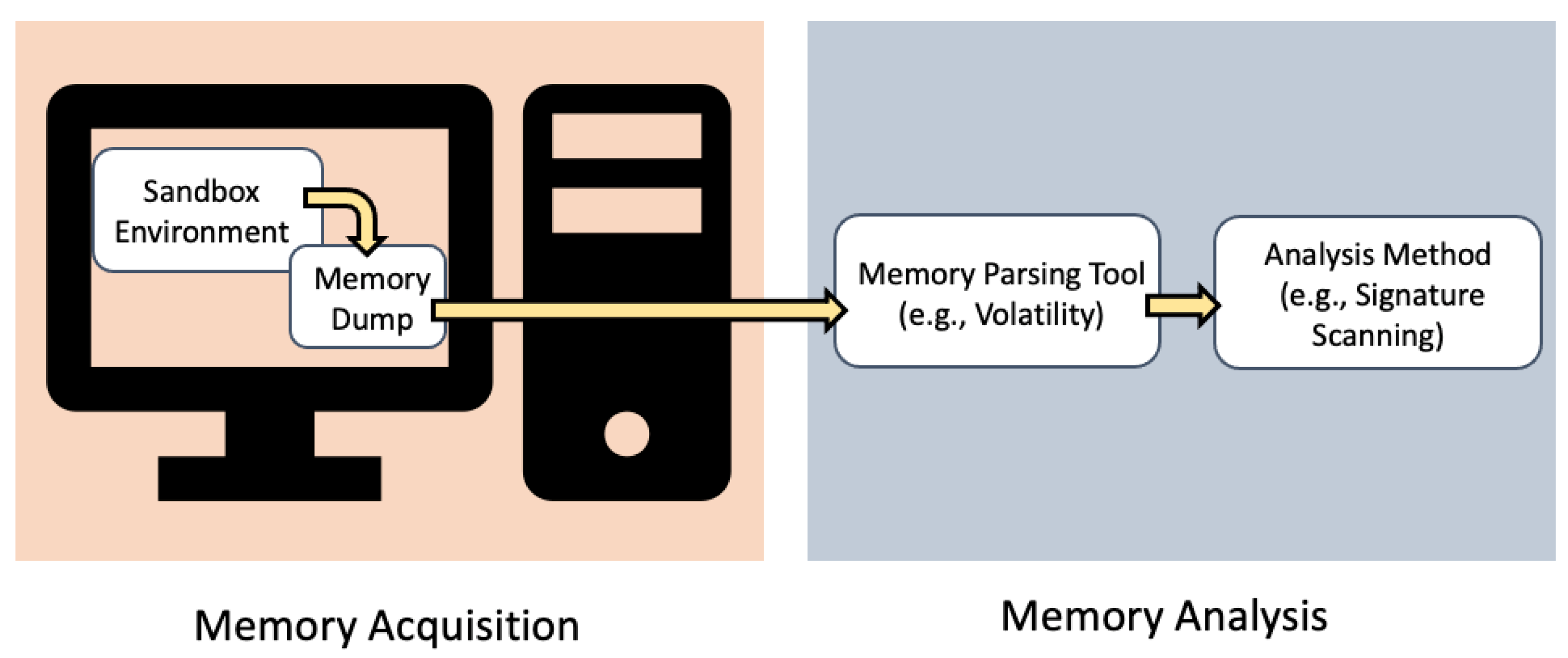
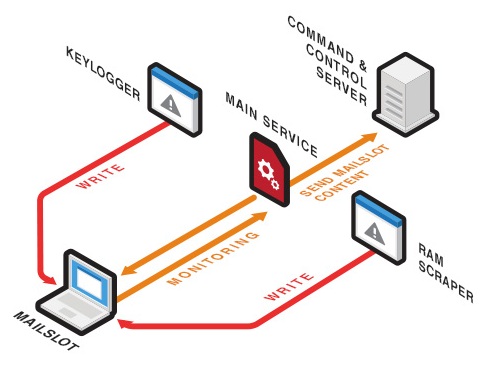
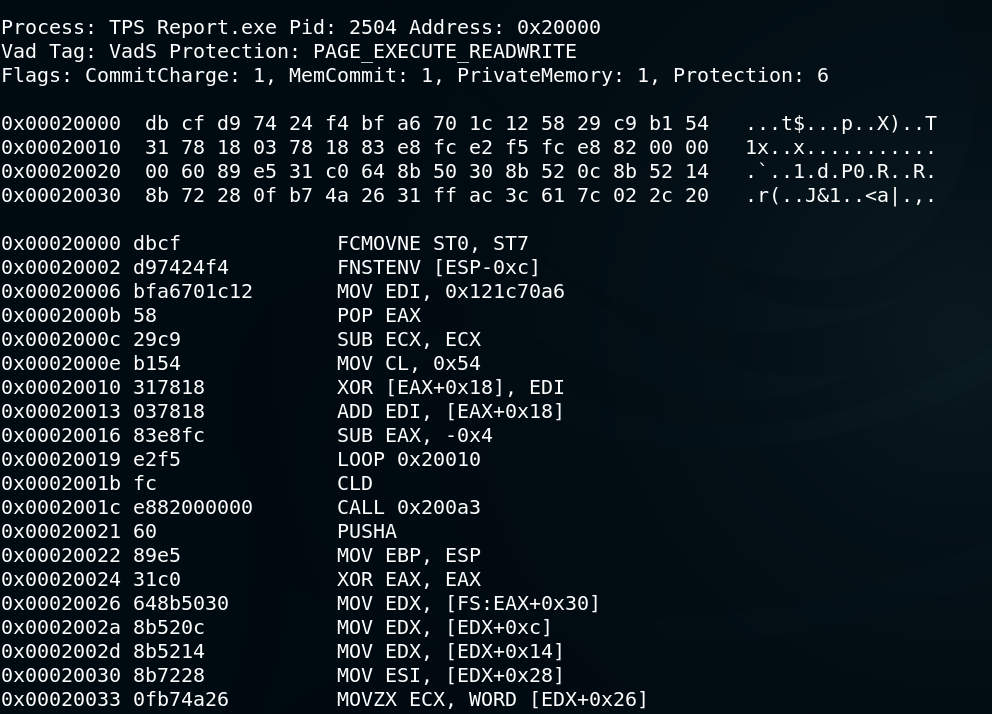
An Identity Based Encryption Scheme Resilient to RAM Scraper Like Malware Attacks: Glassbox Secure IBE

The general flowchart for extracting memory features to create the dataset | Download Scientific Diagram

What Retailers Need to Learn from the Target Breach to Protect against Similar Attacks - Security Intelligence

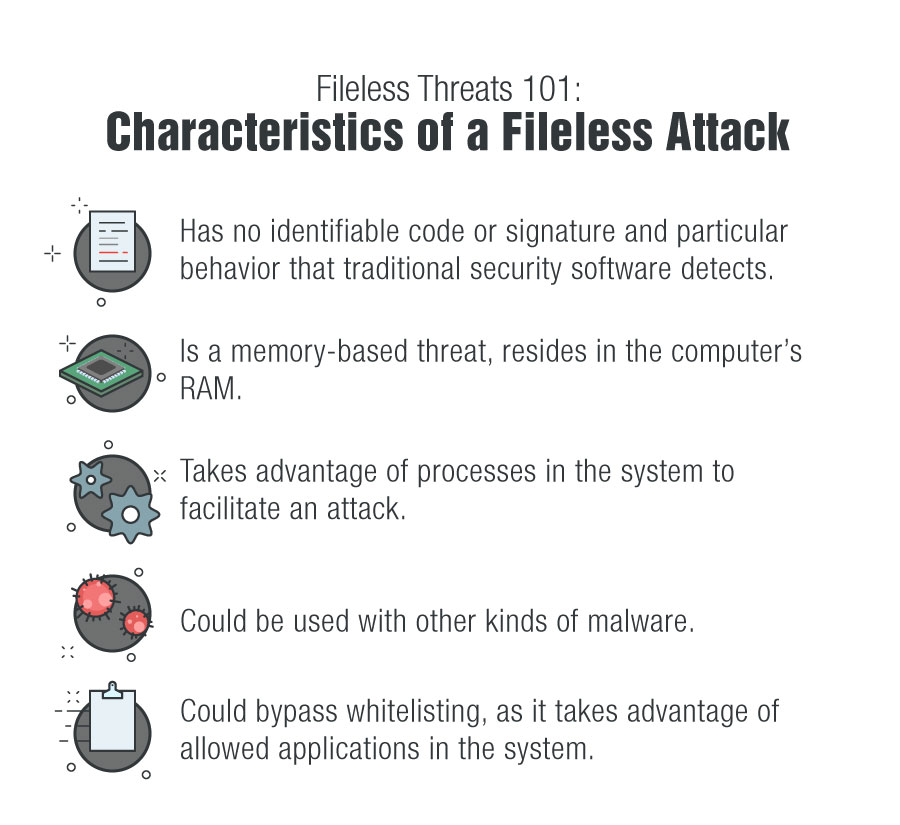
Memory-Resident Malware: What You Should Know - Logix Consulting Managed IT Support Services Seattle

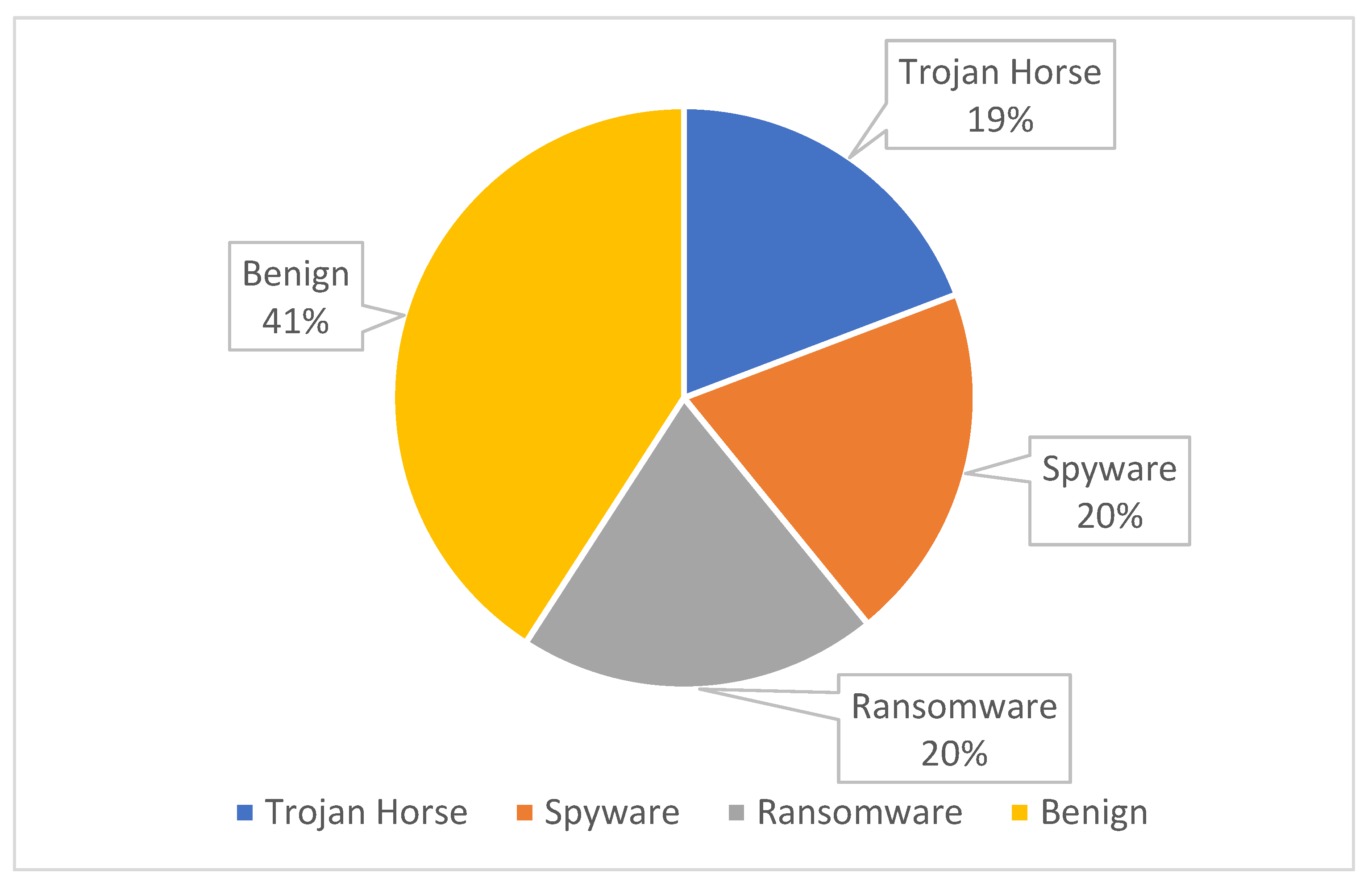










/cdn.vox-cdn.com/uploads/chorus_image/image/63705346/credit_card_swipe.0.1537497931.0.png)